Table of Contents:
- What is the attack called Man in the Middle?
- What does it mean for you in practice?
- Let’s illustrate an example of a Man in the Middle attack:
- Now, what is the difference between encrypted and unencrypted communication?
- Unencrypted Communication (Plain text):
- Encrypted Communication:
- How to defend against the Man in the Middle attack?
- What Is The Attack Called Man In The Middle?
- Conclusion
Last updated December 5th, 2023 23:52
You might have heard of various types of cyber attacks, but what is the attack called Man in the Middle? It is a cunning type of attack that can jeopardize your security and privacy in the online world. Security experts often refer to this attack as one of the most dangerous and well-hidden ones. Let’s take a close look at it.
Imagine you are online, communicating with your bank account, social media, or shopping on an online store. You expect that your data is secure, and no one else but you and the server you are communicating with has access to your information. Unfortunately, the “Man in the Middle” attack disrupts this trust and security.
What is the attack called Man in the Middle?
To better understand it, imagine this scenario: When you visit a website or connect to an online service, your device (e.g., computer or smartphone) communicates with a remote server hosting that service. Your data is transmitted over the internet in the form of small packets. And here lies the problem.
The attacker behind the “Man in the Middle” attack interferes with the communication between your device and the server. In this way, the attacker is literally “in the middle” of the whole process. They can eavesdrop, record, or even modify the data being transmitted between you and the server, without you suspecting a thing.
What does it mean for you in practice?
The attacker can intercept your personal information, such as passwords, banking details, email addresses, or other sensitive data. If you ever enter this information on websites that are not secure (you can identify this by “http://” instead of “https://” in the URL), the attacker has an easy task.
Furthermore, if the attacker gains access to your communication channel, they may even impersonate you and communicate with other people on your behalf. This can lead to misinformation, financial losses, or damage to your reputation.
Let’s illustrate an example of a Man in the Middle attack:
- Company “ABC” specializes in construction projects and development. They have a contract to build a new shopping center and want to collaborate with the client, company “XYZ.”
- Correspondence between company “ABC” and “XYZ” takes place through email messages. Company “ABC” prepares a price offer and project-related documents and sends them to the client’s email.
- Here’s the problem: An attacker, who is aware of the communication between both companies, interferes with this communication without either participant suspecting it.
- The attacker uses sophisticated techniques to eavesdrop on the communication between companies “ABC” and “XYZ.” They can achieve this, for instance, by infiltrating the Wi-Fi network of one of the participants.
- Once the attacker gains access to the communication, they can manipulate the content of emails and even forge them. In this specific case, they decide to alter the price offer from company “ABC” to make it appear less advantageous and more expensive than the genuine offer.
- The attacker then sends the forged price offer to company “XYZ” instead of the original offer from company “ABC.”
- Company “XYZ” receives the modified price offer and takes it as genuine. As a result, they reject the collaboration with company “ABC” because the new project cost exceeds their budget.
- Company “ABC” is now confused when they realize they can’t participate in the project. Only after thorough examination of outgoing emails from both sides, they discover that company “ABC” fell victim to the “Man-in-the-Middle” attack.
Now, what is the difference between encrypted and unencrypted communication?
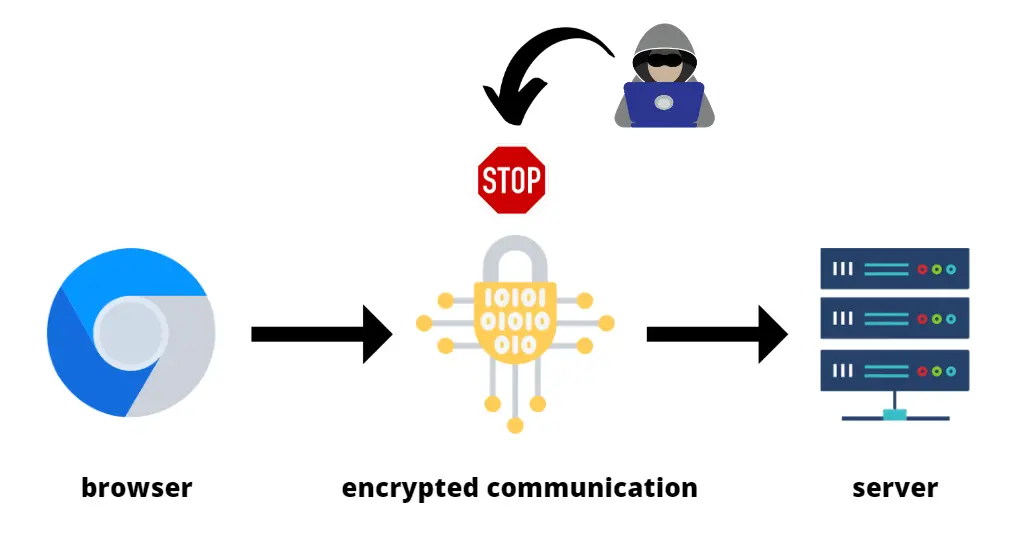
In the world of cybersecurity, encryption plays a crucial role in communication. To better understand what it means and how it relates to the “Man in the Middle” attack, let’s take a closer look.
Unencrypted Communication (Plain text):
When we talk about unencrypted communication, it means that data is transmitted without encryption and is readable by anyone who has access to the communication channel. This communication is similar to writing a message on a postcard that anyone who finds it could read.
In the context of the “Man in the Middle” attack: If we use unencrypted communication and send sensitive data, such as passwords or financial information, the attacker who is “in the middle” of this communication can easily eavesdrop on and misuse this data. They can seize your username and password and gain unauthorized access to your accounts.
Encrypted Communication:
In contrast to unencrypted communication, encrypted communication secures data using mathematical algorithms that transform it into an unreadable format (hash). Encrypted communication is like writing a letter in a code that only someone who knows the correct key can decipher.
In the context of the “Man in the Middle” attack: If we use encrypted communication and send sensitive data, the attacker attempting to eavesdrop would only obtain an unintelligible code. This code (hash) would not be easily decipherable. This makes it difficult for the attacker to exploit this data.
How to defend against the Man in the Middle attack?
- Use encrypted communication: Prefer websites and applications that use the HTTPS protocol for secure communication. This protocol ensures that data is encrypted during transmission, minimizing the risk of eavesdropping.
- Verify certificates: When accessing websites, verify if they have a valid HTTPS certificate. Avoid entering sensitive information on unsecured websites.
- Avoid public Wi-Fi networks: Refrain from connecting to public Wi-Fi networks. Instead, prefer using your secure mobile data connection or set up your own Wi-Fi network. This is especially important in public Wi-Fi networks found in shopping malls or restaurants. Never perform sensitive actions, like accessing your bank account, through such networks. If needed, switch to a mobile data plan.
- Use a VPN: If you have to use public Wi-Fi, utilize a Virtual Private Network (VPN). VPN creates an encrypted tunnel between you and the internet, making it difficult for attackers to monitor your communication. Some well-known VPN service providers include Nord VPN.
- Keep software up to date: Always keep your operating systems, browsers, and applications up to date. Manufacturers often release updates that address known vulnerabilities.
- Use strong passwords: Choose strong and unique passwords for your accounts. Use a combination of uppercase and lowercase letters, numbers, and special characters.
- Two-factor authentication: Whenever possible, enable two-factor authentication for your accounts. This additional layer of security makes it harder for attackers to gain unauthorized access, even if they acquire your password. Store backup codes in a secure place, preferably offline.
- Verify data before submission: Before submitting sensitive information (e.g., payments, personal details), always ensure you are on a secure page and communicating with a legitimate server.
What Is The Attack Called Man In The Middle?
Conclusion
Today, we have described the Man-in-the-Middle attack. It is the most widespread type of attack, along with phishing. In the next chapters of this category, we will further explore social engineering or various types of attacks such as phishing, vishing, spear phishing, and many others. The better you understand potential attacker techniques, the easier it will be for you to detect such activities.
The website is created with care for the included information. I strive to provide high-quality and useful content that helps or inspires others. If you are satisfied with my work and would like to support me, you can do so through simple options.
Byl pro Vás tento článek užitečný?
Klikni na počet hvězd pro hlasování.
Průměrné hodnocení. 0 / 5. Počet hlasování: 0
Zatím nehodnoceno! Buďte první
Je mi líto, že pro Vás nebyl článek užitečný.
Jak mohu vylepšit článek?
Řekněte mi, jak jej mohu zlepšit.

Subscribe to the Newsletter
Stay informed! Join our newsletter subscription and be the first to receive the latest information directly to your email inbox. Follow updates, exclusive events, and inspiring content, all delivered straight to your email.
Are you interested in the WordPress content management system? Then you’ll definitely be interested in its security as well. Below, you’ll find a complete WordPress security guide available for free.

