Table of Contents:
- How to mitigate a brute force attack on WordPress – 3 proven methods
- Method 1 – Disable user enumeration
- Method 2 – Change the administration URL
- Method 3 – Set up login attempt limits
- Tip for experts – brute force attacks and the admin user
WordPress is a system currently used by approximately 40% of websites worldwide. Due to its widespread use, it is also a relatively common target for hackers seeking to access your data or simply damage your website. A brute force attack is a technique where a hacker tries usernames and passwords repeatedly until they find the correct combination. In this article, we will demonstrate how to mitigate a brute force attack on WordPress using three methods that are effective.
How to mitigate a brute force attack on WordPress – 3 proven methods
Method 1 – Disable user enumeration
I will show you an address that, if not secured in WordPress, will display a list of all users on your system (WordPress Users Disclosure). Feel free to try it out.
domain.tld/wp-json/wp/v2/users/For the domain.tld, be sure to use the name of your own domain. Most likely, WordPress has now shown you the users it has. Why is this a problem? Because a potential attacker already knows the login, and they only need to guess the password. If you don’t have a really strong password, you may be setting yourself up for trouble. However, using a short code, you can block this address so that WordPress users won’t be displayed to anyone.
For inserting code into your website, I recommend the excellent WPCode plugin. If you’re interested in how this plugin works, take a look at my article where I write about it: How to Insert Custom Codes in WordPress.
Use this plugin to insert the following code into your website:
add_filter('rest_endpoints', function ($endpoints) {
if (isset($endpoints['/wp/v2/users'])) {
$endpoints['/wp/v2/users'] = [
'methods' => 'GET',
'callback' => function () {
return new WP_Error('forbidden', 'Unauthorized', ['status' => 403]);
}
];
}
return $endpoints;
});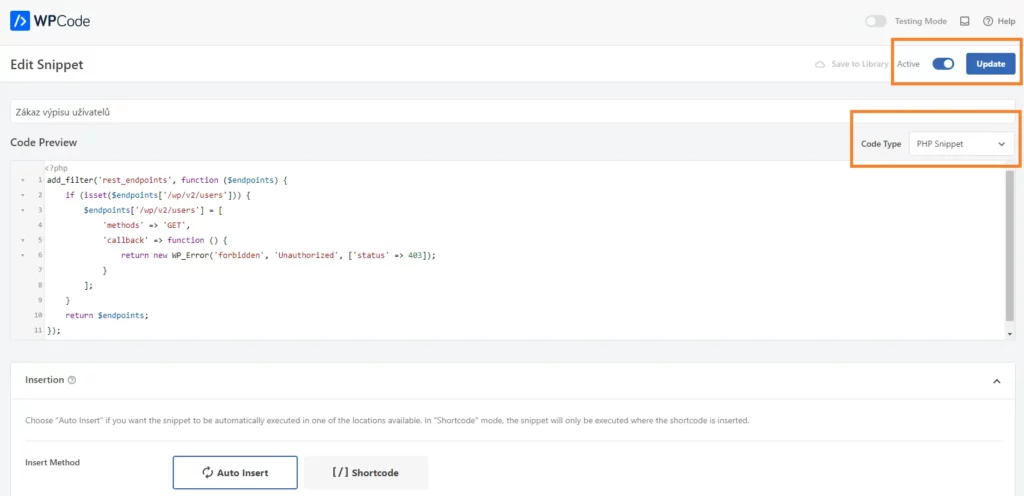
Once you activate and save the snippet, the user listing address will be inaccessible.
Method 2 – Change the administration URL
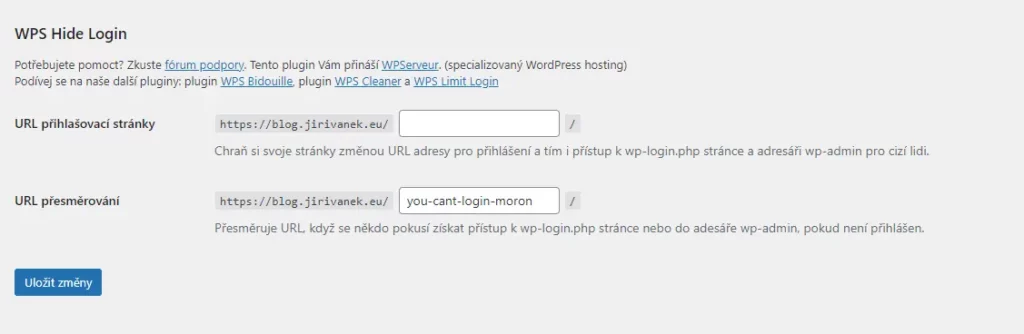
WordPress has two possible paths for accessing the administration panel. One is domain.tld/wp-admin, and the other is domain.tld/login.php. An attacker attempting to target your website using a brute force attack will likely use one of these two addresses as their initial point of entry. Therefore, it is a good idea to change the URL. To modify the URL address, you can use the WPS Hide Login plugin. It is very straightforward, and after activation, it adds a section to your WordPress settings under the General tab where you can define your custom administration URL. Additionally, you can set a second address to which users attempting to access the administration panel through the conventional path will be redirected.
Now you are in a phase where a potential attacker doesn’t know any WordPress users and doesn’t even know the address of your administration panel.
Method 3 – Set up login attempt limits
The last method that will make it more difficult to reveal your password involves limiting the number of login attempts. This can be achieved conveniently using the Limit Login Attempts Reloaded plugin. Among other features, this plugin allows you to configure the following:
- Login Limit – Restricts the number of login attempts (per IP address).
- Adjustable Lockout Duration – Modifies the duration a user or IP address must wait after a lockout.
- Remaining Attempts – Informs users about the remaining login attempts or the lockout duration on the login page.
- Lockout Notification via Email – Notifies administrators by email about lockouts.
- Records of Unsuccessful Attempts – Displays records of all rejected attempts and lockouts.
- Whitelist/Blacklist IP addresses and usernames – Controls access to usernames and IP addresses.
- XMLRPC Gateway Protection.
- Woocommerce Login Page Protection.
As you can see, with this plugin, you can configure a lot. If it doesn’t suit your needs, there are other plugins available in the WordPress repository that offer similar functionalities. It is crucial to block a user who attempts an excessive number of login requests early on.
Tip for experts – brute force attacks and the admin user
The final piece of advice is something I’ve explained several times on this blog. Do not create a user named admin. It is the first user an attacker will try. Instead, name your administrative user differently. By doing so, you take away the attacker’s chance of discovering your users right from the start because a user with the login admin simply won’t exist in the system.
If you apply all the principles mentioned above to your website, I dare say that in the case of brute force attacks, your website will be perfectly prepared, prompting such attackers to seek fortune elsewhere.
The website is created with care for the included information. I strive to provide high-quality and useful content that helps or inspires others. If you are satisfied with my work and would like to support me, you can do so through simple options.
Byl pro Vás tento článek užitečný?
Klikni na počet hvězd pro hlasování.
Průměrné hodnocení. 0 / 5. Počet hlasování: 0
Zatím nehodnoceno! Buďte první
Je mi líto, že pro Vás nebyl článek užitečný.
Jak mohu vylepšit článek?
Řekněte mi, jak jej mohu zlepšit.

Subscribe to the Newsletter
Stay informed! Join our newsletter subscription and be the first to receive the latest information directly to your email inbox. Follow updates, exclusive events, and inspiring content, all delivered straight to your email.
Are you interested in the WordPress content management system? Then you’ll definitely be interested in its security as well. Below, you’ll find a complete WordPress security guide available for free.

